Unlocking Access with Azure Key Vault | PwnedLabs
Lab Description
After successfully compromising the Azure user account marcus@megabigtech.com and gaining access to their cloud environment, Mega Big Tech have asked us to see how far we can penetrate into the cloud environment, and if we can access any confidential data. Specifically they need us to assess the security of resources associated with the Azure Subscription ID ceff06cb-e29d-4486-a3ae-eaaec5689f94.
Learning Outcomes
- Azure Cloud Security
- Enumeration for situational awareness and lateral movement
- Accessing secrets in Azure Key Vault
- Querying data in Azure Storage Tables
Real-World Application
Azure Key Vaults are one of many key management solutions in Azure, and they are important for Secrets Management, Key Management, and Certificate Management. As you can see, Azure Key Vaults can store sensitive data like secrets, keys, and certificates, so Azure Key Vaults are a prime target for attackers. This lab focuses on principle of least privelege as it relates to contractor accounts, since if contracotr accounts have high priveleges and aren’t properly secured, attackers can compromise the account and move through the Azure account to access confidential data in Azure Key Vaults.
Lab Walkthrough:
Before starting the lab, PowerShell, Azure CLI, and Microsoft Graph PowerShell SDK needs to be installed. Once those are installed, we can start the attack part of the lab.
Attack:
First, we need to log into Azure with the credentials given to us for the lab:
Azure Credentials:
- IAM User: marcus@megabigtech.com
- Password: TheEagles12345!
- https://portal.azure.com/
Command for logging into Azure user through CLI:
1
az login
Once this is entered, we are taken to Azure login portal:
Log in as marcus@megabigtech.com and we will see authentication success:
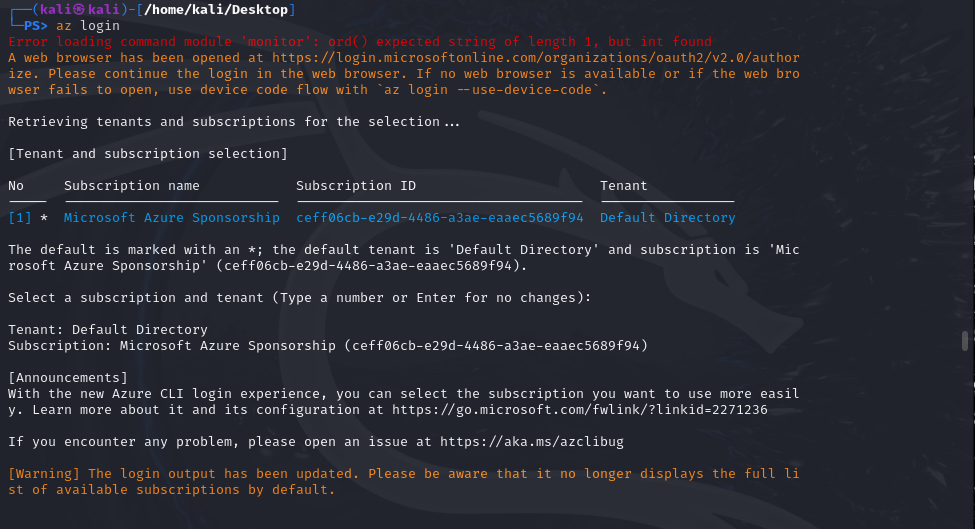
Now, back to the CLI, we are logged in as the compromised account:
In Azure AD, there’s a command for showing more information about the current signed-in user in the CLI. This command is:
1
az ad signed-in-user show
We will enter this command to get more details on the user we are logged in as just to get more info on the Azure user.
After entering this command we see the user’s name ‘Marcus Hutch’ along with some other info. But we want to get to sensitive info in the Azure environmet, so the first thing we should look for is more information on the resources attached to this account. To do that, there is another command in Azure AD:
1
az ad resource list
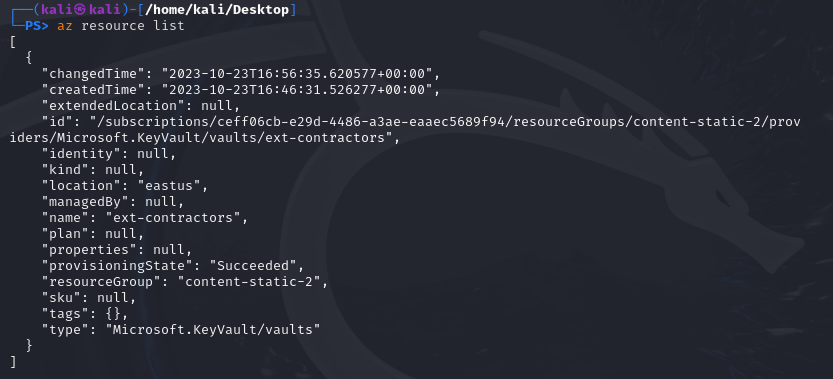
After running this, here’s what we see:
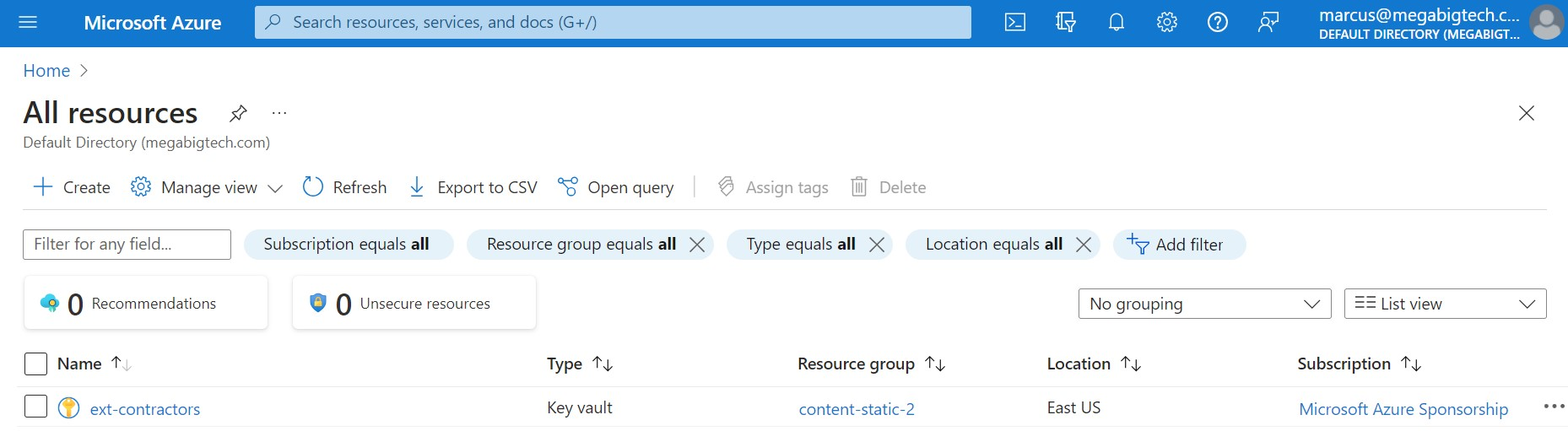
There’s some good info here. First, we can see under the ‘id’ tag ‘Microsoft.KeyVault/vaults/ext-contractors’ which lets us know that the Azure Key Vault is called ‘ext-contractors’. As mentioned earlier, any sensitive info will be in the Key Vault, so this is our target. We can also tell that this user has access to the Key Vault resource based on the line “type”: “Microsoft.KeyVault/vaults”.
Another thing to note, since we already have access to this user’s Azure credentials for this lab, we can also enumerate through the Azure portal:
- Access: https://portal.azure.com/
Once authenticated, we are in the Azure portal, and can access the resources we saw from running ‘az ad resource list’ in the CLI:
Resources: